Dynamic Configs for the Hammer 88
I already wrote about how to back up a MIDI instrument by reverse-engineering SysEx messages using Wireshark. This time, our target is the M-Audio Hammer 88 MIDI keyboard.
Unlike the Novation Circuit, they have a neat, native Windows app available to tweak settings (like MIDI channels, how to split / transpose keys, etc.). You can load and save presets with little effort; furthermore, they don't even want all your contact info to let you use it. However... wouldn't it be nice to have some keys on a MIDI controller, assigned in your DAW, to reconfigure it on the fly? Maybe it's also just about sending a few SysEx messages?
Well, fortunately, the wave of overengineered, custom garbage have not reached these MIDI instruments yet. It is just about sending a few SysEx messages. This is how we send out the settings to the device:
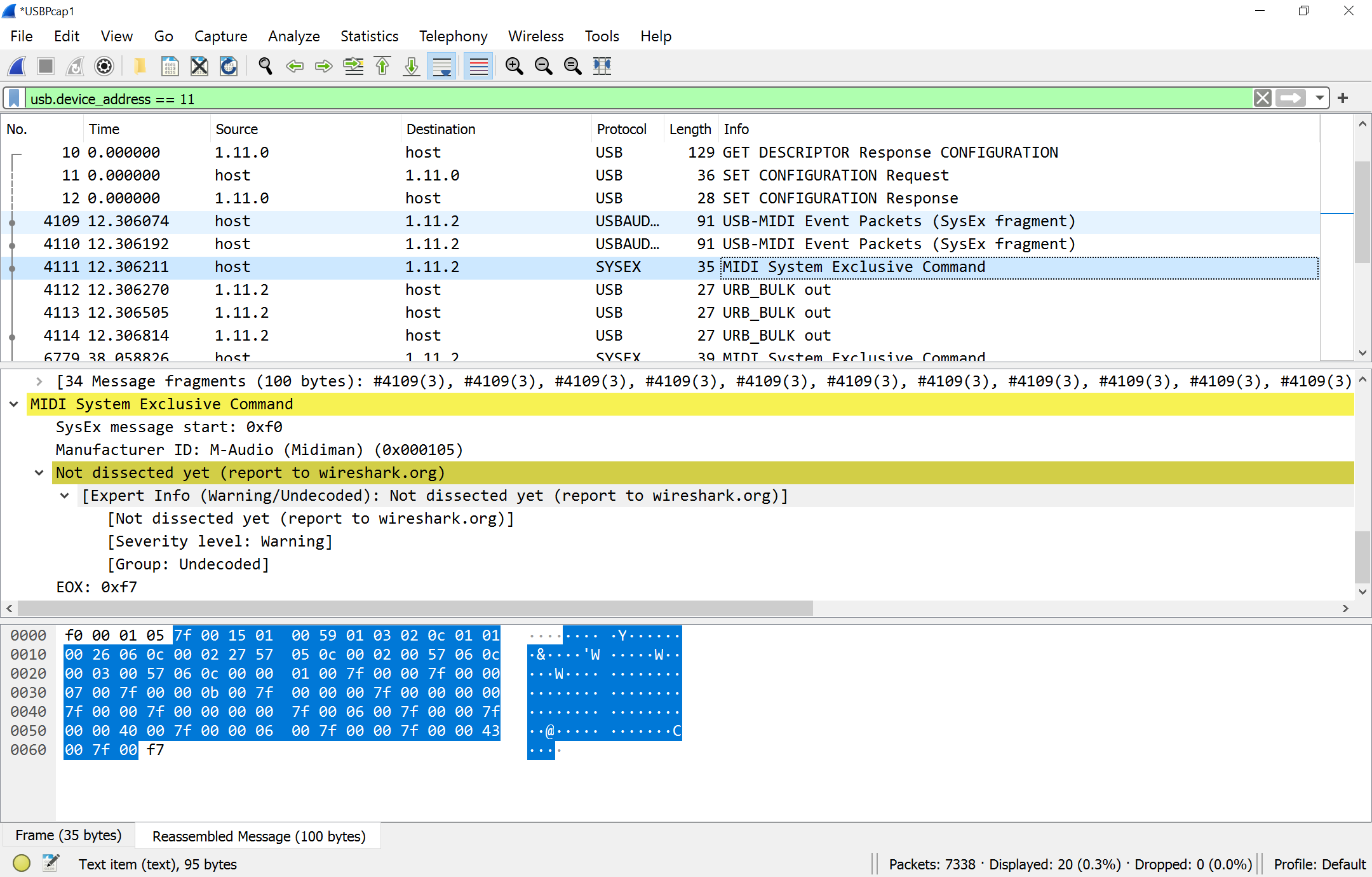
... and here is how we request it back:
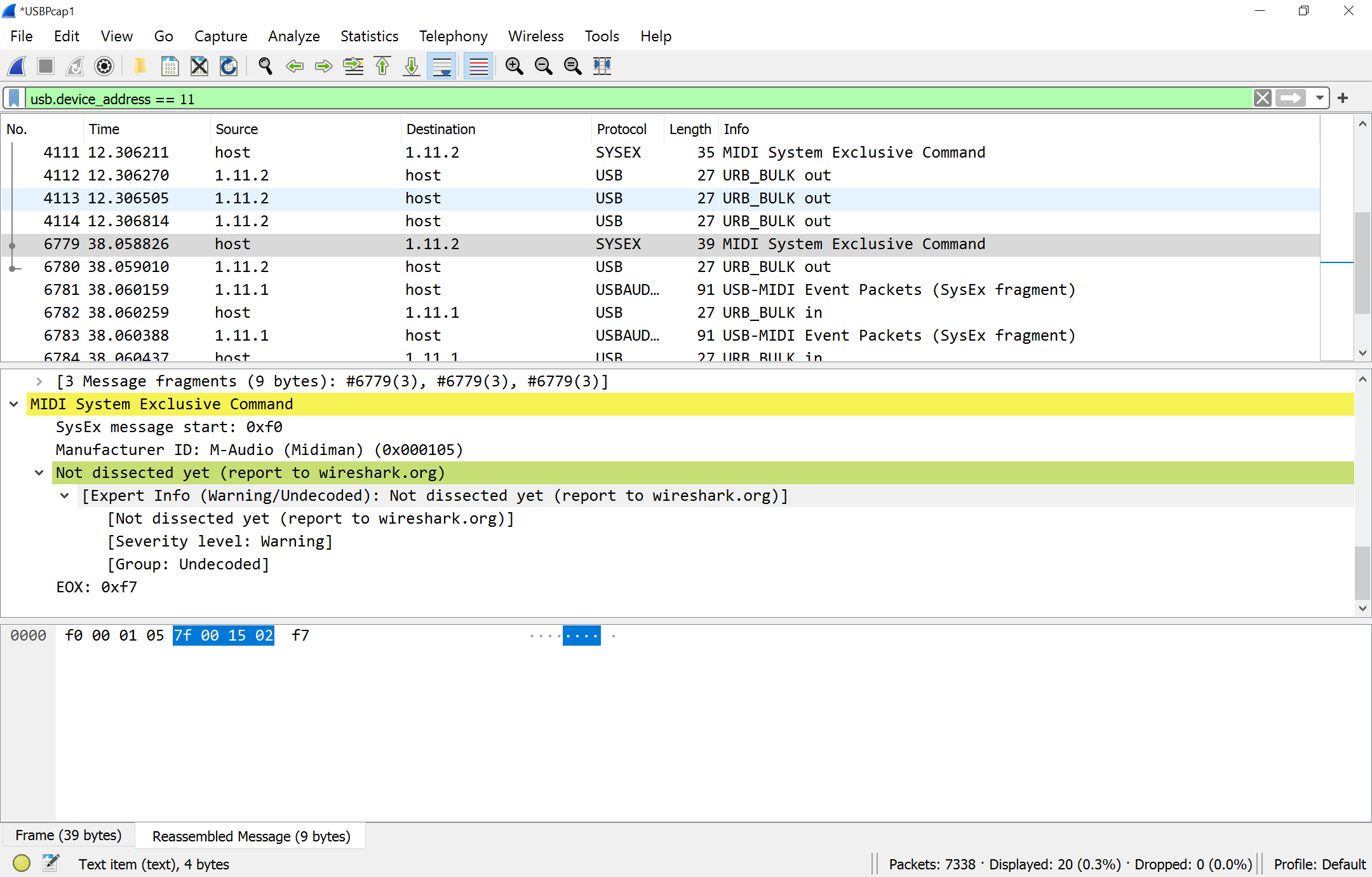
... to which the device answers:
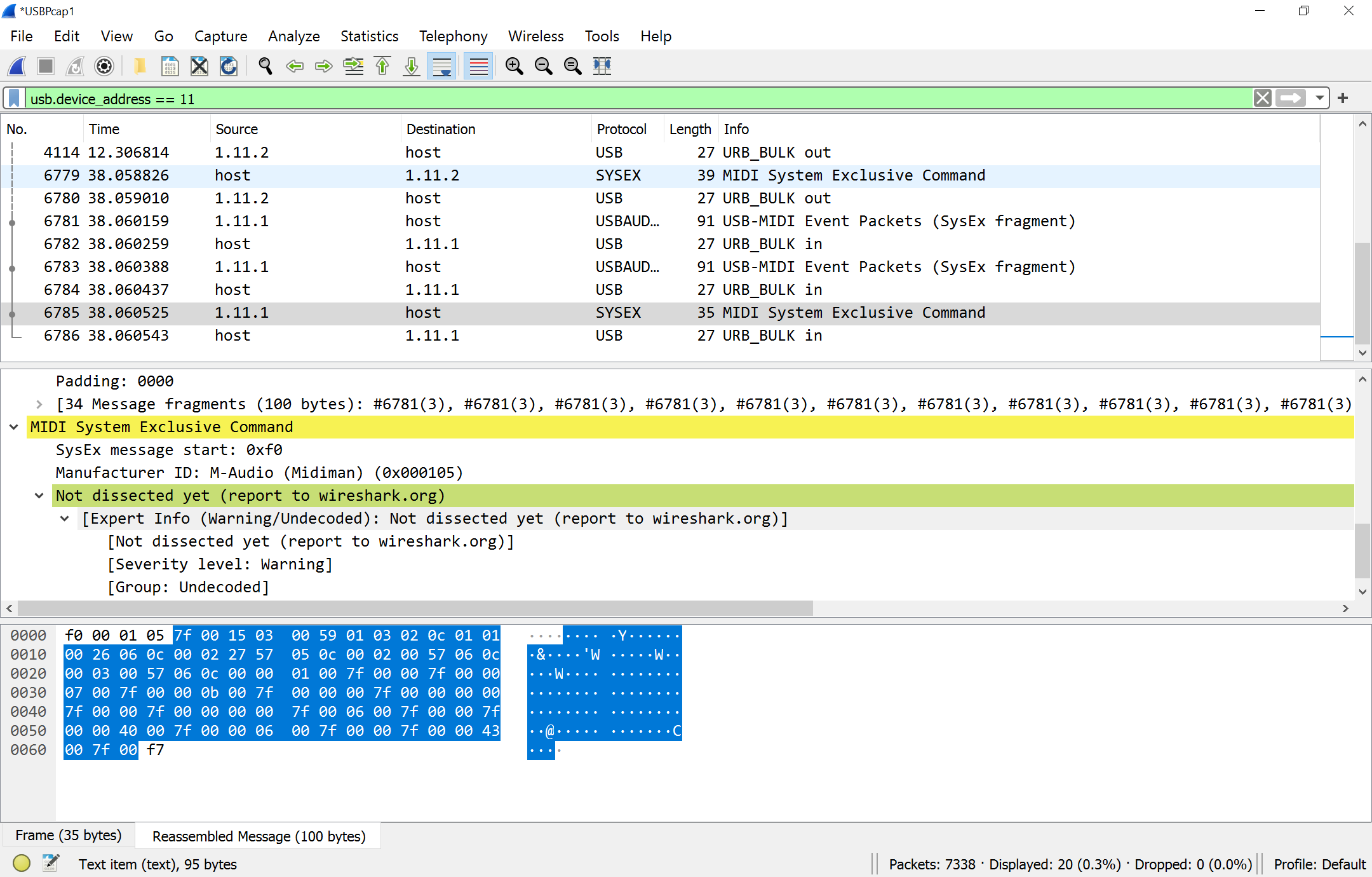
So far, it looks like this has nothing to do with the actual files the tool saves, but... oh well, not everything can be perfect.
Trying it out
So let's follow the next step: try it out with actual MIDI commands!
~ $ amidi -l
Dir Device Name
IO hw:1,0,0 Hammer 88 MIDI 1
~ $ amidi -p hw:1,0,0 -S "f0 00 01 05 7f 00 15 02 f7" -d
F0 00 01 05 7F 00 15 03 00 59 01 03 02 0C 01 01 7 57 05 0C 00 02 00 57 06 0C 00
03 00 57 06 0C 0 7F 00 00 07 00 7F 00 00 0B 00 7F 00 00 00 7F 007F 00 00 00 00
7F 00 06 00 7F 00 00 7F 00 00 40 F 00 00 7F 00 00 43 00 7F 00 F7^C
100 bytes read
... aaand it works!
... saving it:
~ $ amidi -p hw:1,0,0 -S "f0 00 01 05 7f 00 15 02 f7" -r target.syx
Similarly, uploading data:
~ $ amidi -p hw:1,0,0 -s target.syx
So, we can now just set up all the presets that we want to switch between, download them to the keyboard one by one, save them by loading them back on the command line, and restore them easily. For this, we don't even have to figure out the save file format the Windows app is using (... although, to me, it looks very similar to the actual SysEx format, swapping out 2-byte integers to 4 byte ones or something like that.)
What next
Well, we'd like to bind restoring these dumps to MIDI controller keys. Which... I'll still need to figure how to do. Nevertheless, looks like the general Wireshark method of catching messages sent by vendor-supplied apps has worked yet again!
... comments welcome, either in email or on the (eventual) Mastodon post on Fosstodon.